Authentication
There are several ways to provide authentication with your pathfinder application depending on the developer's needs. Pathfinder supports ready to use authentication but allows developers to use their own custom authentication.
Authentication Flow
Which ever authentication scheme you use for your application, the general flow is relatively the same.
-
When the client attempts to connect to the Pathfinder service, Pathfinder responds with a randomly generated, unique connection id.
-
This connection id, along with data identifying the user, is then sent to a server responsible for authenticating users.
-
Once the authentication server is ready, the client sends an authenticate message back to the Pathfinder service.
-
The Pathfinder service then sends a request to the authentication server to determine of it is okay to allow the user to open the connection.
-
If that is successful, an authenticated message is sent back to the client and then the client can start using the developer's Pathfinder data.
Using Pathfinder Authentication
Pathfinder provides ready to go authentication. All the developer has to do is configure the application's authentication settings through the application dashboard. By default, Pathfinder uses google openid connect tokens to identify users. The client must get the user's openid connect token and then provide it to the SDK. The process of obtaining an open id connect token is shown here. How to use the id tokens is shown below.
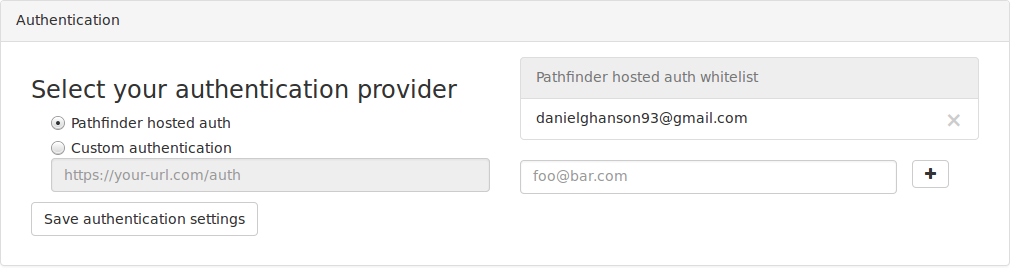
Permissions
The application dashboard allows the developer to set up a white list of email addresses of users who have access to the application data stored by pathfinder. This includes all of the clusters, transports, and commodities in the application.
Custom Authentication
The Pathfinder API also allows the developer to roll their own authentication. They just need to implement their own authentication endpoint and configure their application to use it. Note that the permissions set on the dashboard only apply to Pathfinder authentication. If you decide to use custom authentication, then the endpoint you've set up to handle authentication needs to be able to handle permissions.
Custom Authentication Flow
Custom authentication is more involved since it requires setting up your own authentication server and requires a few extra steps to use the SDKs.
The SDKs allow you to specify what happens when a user attempts to use Pathfinder. For custom authentication, your app should send user information along with the received connection id to your authentication server. From this, the authentication server should prepare to response to a connection request from the api server. Through the response, the authentication server indicates whether the user trying to use Pathfinder is authorized to. The url of your authentication server is specified using the authentication configurations on the Pathfinder dashboard.
Once it is configured, the api server sends a get request to the specified url whenever a Pathfinder client requests authentication.
GET www.my_auth_server.com/connection?connection_id=cfc85366-a8f3-42a8-ad7d-95537a8cd18e&application_id=9869bd06-12ec-451f-8207-2c5f217eb4d0 HTTPS/1.1
It has two query parameters, connection_id and application_id. Once your server receives this request, it needs to respond with a Pathfinder JWT signed with your private key.
header = {
"alg": "HS256",
"typ": "JWT"
}
payload = {
"aud":"https://api.thepathfinder.xyz",
"iss":your_app_id,
"exp":1461549610,
"sub":connection_id,
}
Pathfinder then should be ready to use
Updated less than a minute ago
